Configure Cloud Credentials
Set up secure access to your AWS and GCP accounts for infrastructure management
Overview
Infra.new requires cloud credentials to interact with your AWS or GCP resources. These credentials enable:
- Resource Import: Discover and generate Terraform code for existing cloud resources
- State Backend Monitoring: Track changes to your Terraform state files
- Infrastructure Deployment: Apply Terraform configurations to your cloud accounts
Security Best Practices
💡 Follow these security principles:
- Least Privilege: Grant only the minimum permissions required
- Separate Credentials: Use different credentials for dev/staging/prod
- Regular Rotation: Rotate access keys periodically
- Audit Access: Review credential usage regularly
- Never Share: Keep credentials secure and never commit to version control
Credential Setup
Choose your cloud provider below for detailed setup instructions:
AWS Permission Requirements
Different features require different permission sets
For Resource Import
To discover and import existing AWS resources:
ResourceExplorer2ReadOnlyAccessAllows discovery of resources across your account
ReadOnlyAccessProvides read access to retrieve resource configurations
For State Backend Monitoring
To monitor Terraform state files in S3:
AmazonS3ReadOnlyAccessQuick option: Grants read access to all S3 buckets
More secure: Limits access to specific bucket
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Action": ["s3:GetObject", "s3:ListBucket"],
"Resource": [
"arn:aws:s3:::YOUR_STATE_BUCKET",
"arn:aws:s3:::YOUR_STATE_BUCKET/*"
]
}]
}Step-by-Step Setup
1. Navigate to IAM
- Open the AWS Console
- Navigate to the IAM service
- Select Users from the left navigation
- Click Create user
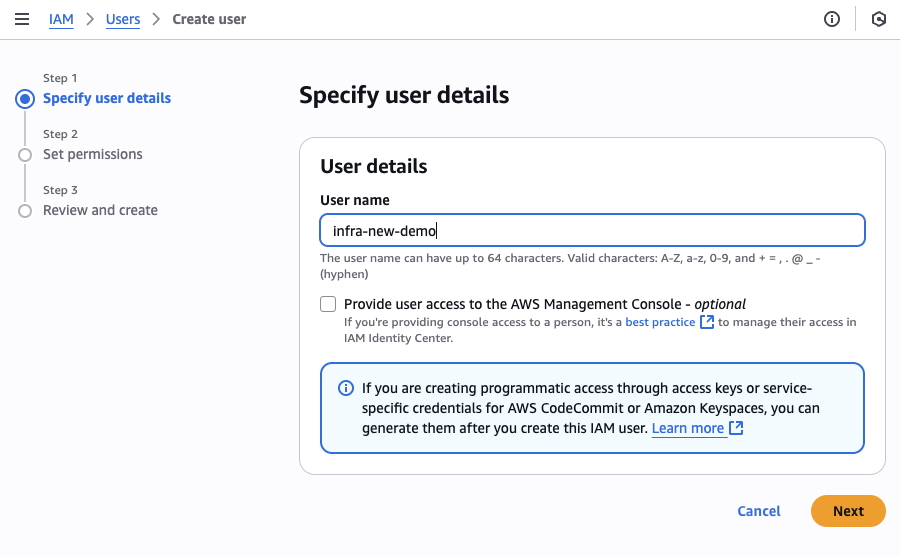
2. Configure User Details
- Enter a descriptive user name:
- For imports:
infranew-import-reader - For state monitoring:
infranew-state-reader
- For imports:
- Select Access key - Programmatic access
- Click Next: Permissions
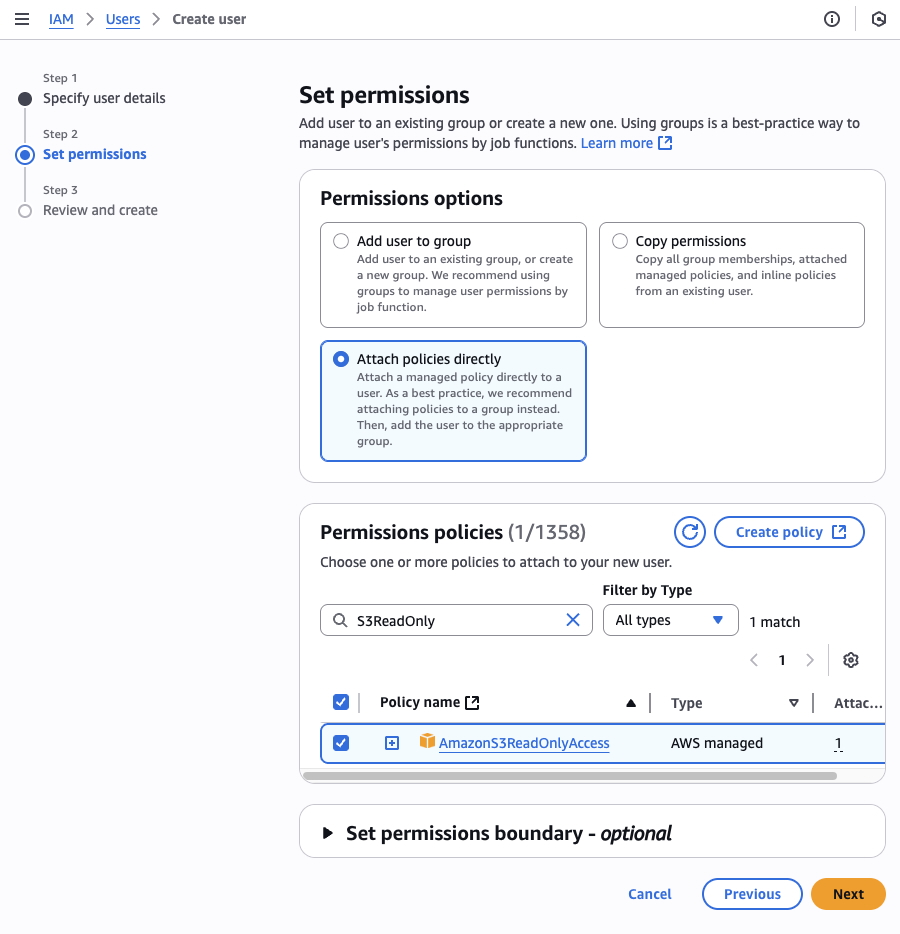
3. Attach Permissions
Based on your use case, attach the appropriate policies:
- Search for the required policy names in the search box
- Select the checkbox next to each policy
- Click Next to continue
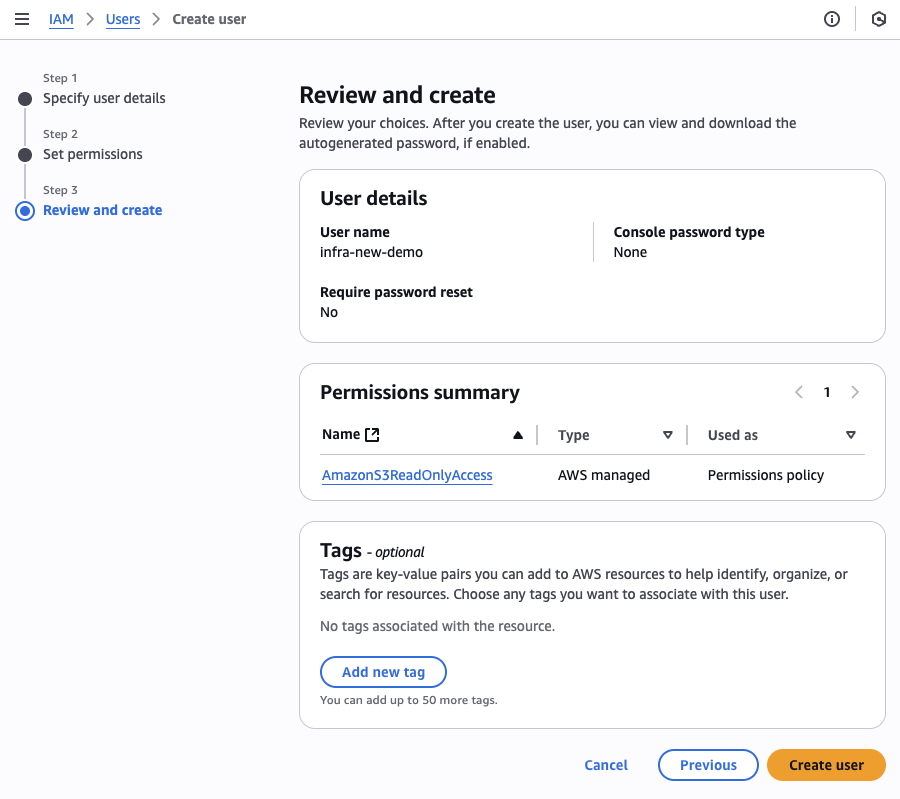
4. Review and Create
- Review the user configuration
- Verify the attached policies are correct
- Click Create user
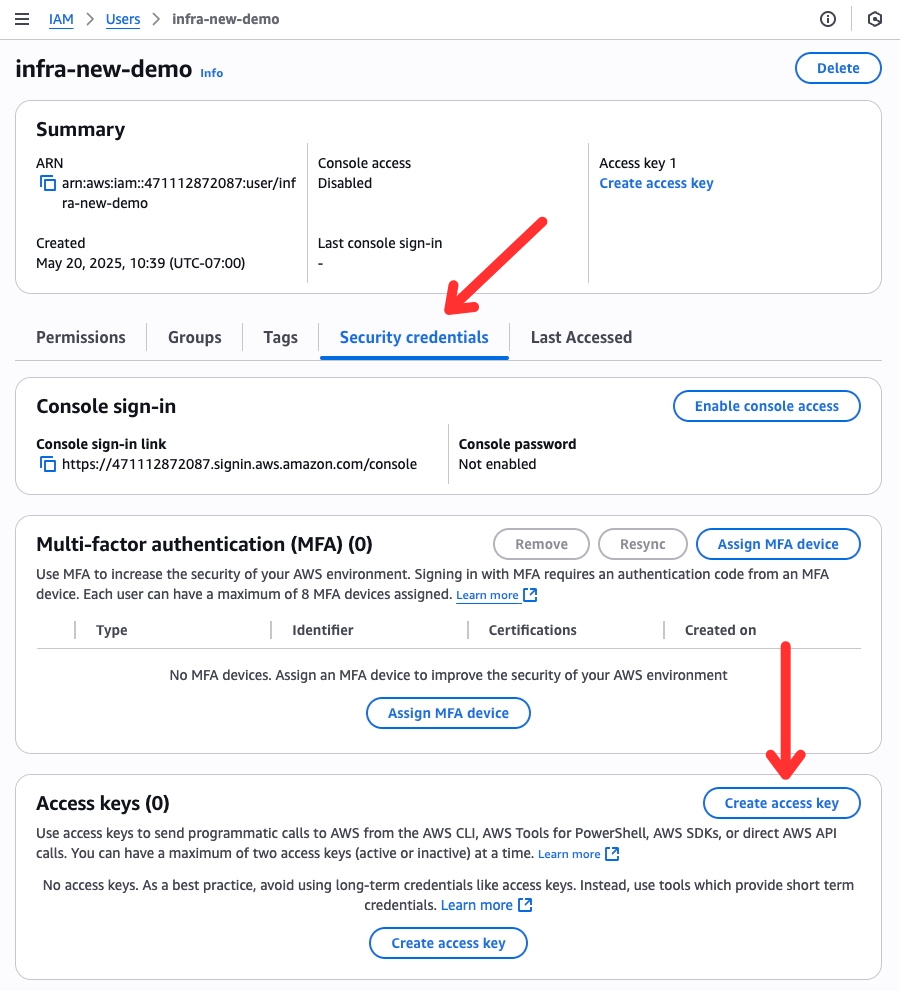
5. Create Access Keys
- Click on the newly created user to view details
- Navigate to the Security credentials tab
- In the Access keys section, click Create access key
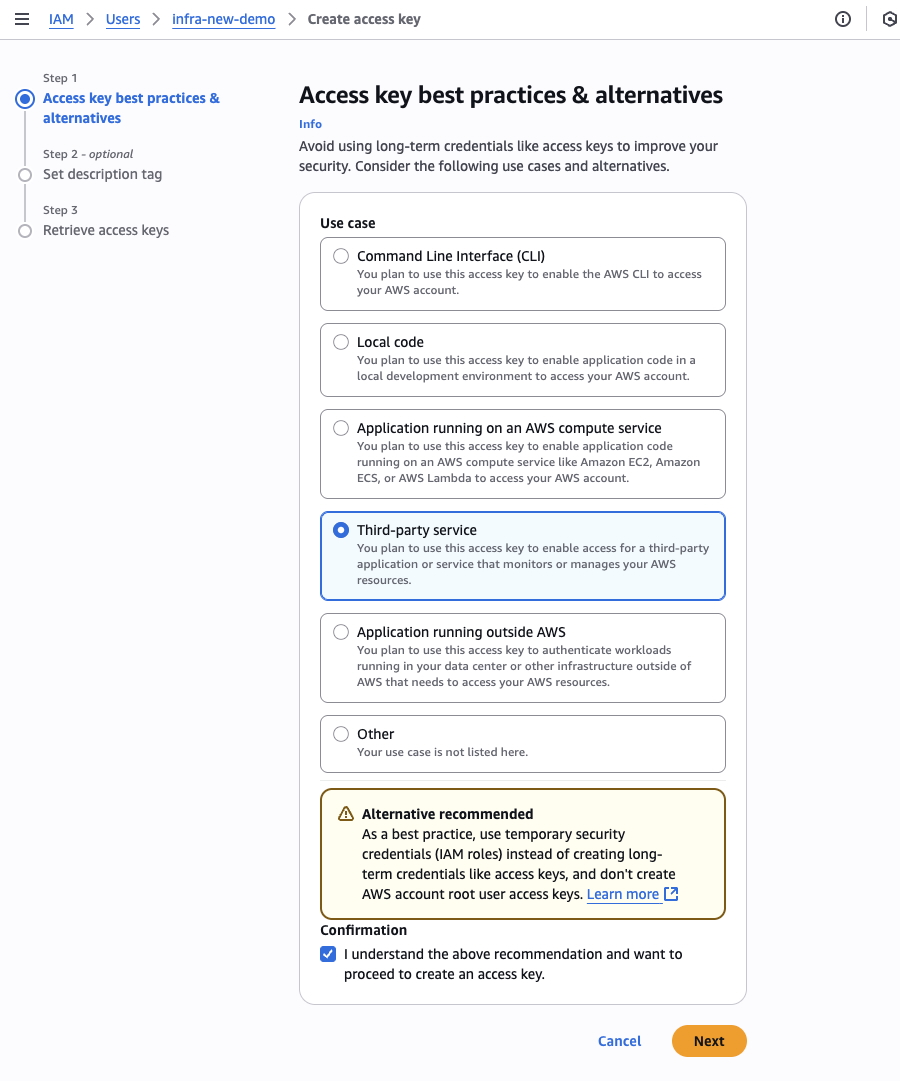
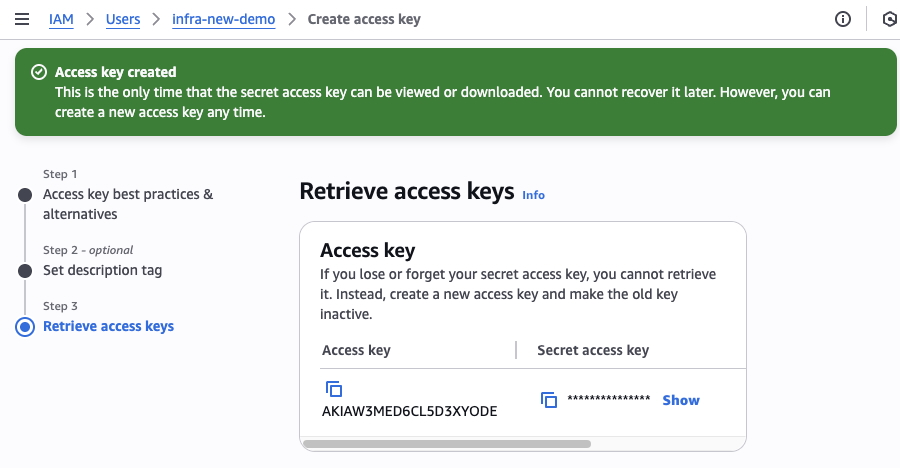
6. Save Your Credentials
Copy and securely save both the Access Key ID and Secret Access Key.
⚠️ Important: This is the only time you can view the Secret Access Key
Store these credentials securely. You'll need them to configure Infra.new.
7. Additional Setup for Resource Import
If using credentials for resource import:
You must also enable AWS Resource Explorer:
- Navigate to AWS Resource Explorer in the console
- Click Turn on Resource Explorer
- Select Quick setup
- Choose an aggregator region (typically us-east-1)
- Click Turn on
Note: Initial indexing takes 15-30 minutes to complete.
Next Steps
Now that you have AWS credentials, you can:
Configure Cloud Credentials
Set up secure access to your AWS and GCP accounts for infrastructure management
Overview
Infra.new requires cloud credentials to interact with your AWS or GCP resources. These credentials enable:
- Resource Import: Discover and generate Terraform code for existing cloud resources
- State Backend Monitoring: Track changes to your Terraform state files
- Infrastructure Deployment: Apply Terraform configurations to your cloud accounts
Security Best Practices
💡 Follow these security principles:
- Least Privilege: Grant only the minimum permissions required
- Separate Credentials: Use different credentials for dev/staging/prod
- Regular Rotation: Rotate access keys periodically
- Audit Access: Review credential usage regularly
- Never Share: Keep credentials secure and never commit to version control
Credential Setup
Choose your cloud provider below for detailed setup instructions:
AWS Permission Requirements
Different features require different permission sets
For Resource Import
To discover and import existing AWS resources:
ResourceExplorer2ReadOnlyAccessAllows discovery of resources across your account
ReadOnlyAccessProvides read access to retrieve resource configurations
For State Backend Monitoring
To monitor Terraform state files in S3:
AmazonS3ReadOnlyAccessQuick option: Grants read access to all S3 buckets
More secure: Limits access to specific bucket
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Action": ["s3:GetObject", "s3:ListBucket"],
"Resource": [
"arn:aws:s3:::YOUR_STATE_BUCKET",
"arn:aws:s3:::YOUR_STATE_BUCKET/*"
]
}]
}Step-by-Step Setup
1. Navigate to IAM
- Open the AWS Console
- Navigate to the IAM service
- Select Users from the left navigation
- Click Create user

2. Configure User Details
- Enter a descriptive user name:
- For imports:
infranew-import-reader - For state monitoring:
infranew-state-reader
- For imports:
- Select Access key - Programmatic access
- Click Next: Permissions

3. Attach Permissions
Based on your use case, attach the appropriate policies:
- Search for the required policy names in the search box
- Select the checkbox next to each policy
- Click Next to continue

4. Review and Create
- Review the user configuration
- Verify the attached policies are correct
- Click Create user

5. Create Access Keys
- Click on the newly created user to view details
- Navigate to the Security credentials tab
- In the Access keys section, click Create access key


6. Save Your Credentials
Copy and securely save both the Access Key ID and Secret Access Key.
⚠️ Important: This is the only time you can view the Secret Access Key
Store these credentials securely. You'll need them to configure Infra.new.

7. Additional Setup for Resource Import
If using credentials for resource import:
You must also enable AWS Resource Explorer:
- Navigate to AWS Resource Explorer in the console
- Click Turn on Resource Explorer
- Select Quick setup
- Choose an aggregator region (typically us-east-1)
- Click Turn on
Note: Initial indexing takes 15-30 minutes to complete.
Next Steps
Now that you have AWS credentials, you can: